So this was a weird one. Remote desktop stopped working on client machines. Troubleshooting led to a group policy Block rule in the Windows firewall but there was no such GPO setting.
TLDR: Don’t put any spaces in the IP address list for the GPO setting for Computer/Admin Templates/Network/Network Connections/Windows Firewall/Domain Profile/Windows Firewall: Allow inbound Remote Desktop exceptions.
After adding a subnet to the “Windows Firewall: Allow inbound Remote Desktop exceptions” Remote Desktop stopped working.
This is the policy…
Windows Firewall GPO Setting
And this is the setting applied adding a second subnet into the Allow unsolicited incoming messages from these IP addresses…
Windows Firewall Setting
After troubleshooting I found the cause was the firewall rule on the local machine was now set to “Block”.
Windows Firewall Incorrect Setting
The rule couldn’t be deleted because this rule has been applied by the system administrator and cannot be modified. In other words it was set by a GPO.
The group policy results tool showed no block rules for remote desktop and only the Allow inbound Remote Desktop exceptions shown above. After trying all the common sense tests I removed the second IP address from the policy… and after a GPUPDATE the firewall rule changed back to Allow….
Windows Firewall Correct Setting
This was unexpected…. so I added the second address in again and the rule changed back to “Block”.
As a further test I changed the rule to an allow all “*” which also worked correctly setting the rule to “Allow”.
On a hunch I added both subnets back in and removed the “good formatting” space between them… and the rule worked properly and set to allow.
Windows Firewall Working Settings
So adding a space into the Allow unsolicited incoming messages from these IP addresses converts the policy from Allow to Block. Weird.
| Works! | Doesn’t Work. |
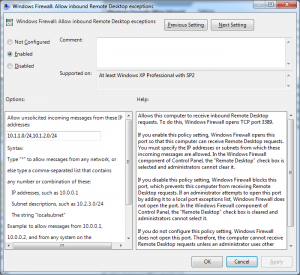 | 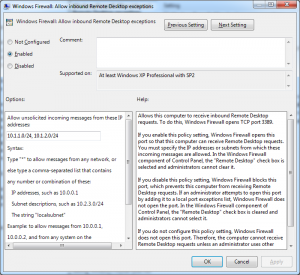 |